
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.
86-0769-39020536
First, the bank needs analysis
The security of the bank is related to the stability of the social economy's lifeblood. The use of a bank security system that combines civil defense, physical defense, and technical defense is particularly important for maintaining the bank's security and stability.
Because the access control system of each branch network branch is built independently, the database cannot be unified, interconnection and sharing cannot be realized for the data collected by the access control across the line, and the access of personnel authorized by the cross-network branch can not be tracked and managed in real time. It is not convenient for the staff and the access control card. Timely management and monitoring work.
The access control management system is at the forefront of bank security prevention work. It is the first barrier to building a high-strength railway network. Building a safe, reliable, defensive-type access control system integrates with the platform of the security management center, which is the most important aspect of bank security system construction. .
Inter-bank authorization complexity The access control cards of each branch cannot be used universally, and authorization is based on independent outlet-level authorization and management. When the VIP customers of banks, the leadership of higher branches direct the work of subordinates, and the work of employees at the same level, the management of authorizations is cumbersome, inconvenient, and unfavorable to the work of the workers in safe and convenient access to restricted areas. It is also not timely and effectively detected and handled. Trouble cards, illegal cards and blacklist cards have brought huge hidden dangers to the bank's access control security.
In addition, common password access control, IC card access control, and fingerprint access control on the market have problems such as easy password leakage, easy copying of IC cards, inconvenient fingerprint collection, etc., and they do not apply to these open public places. Each bank employee must With ID card. Therefore, Shenzhen Yanteng proposed a new solution for these characteristics: Yanteng ID card access control system solution.
Second, the proposal
Project Name: Yanteng Open ID Card Access Control System Solution
The scheme realizes the function:
1. Mass storage function
2. Can be authorized to open the door
3 can open the door independently, do not need to swipe, the administrator opens the door through software control
4. TCP/IP network control
5. Read complete ID information (name, gender, ID number, etc.)
6. Efficient video capture
7. Support independent operation, open the door independent of software autonomous authentication
Third, the program introduced
Yan Teng open ID card access control system comes with large capacity storage function, 500,000 ID card + IC card permissions, 500,000 ID card + IC card records, 30,000 ID card complete information storage, support for reading the complete ID card information ( ID number, photo, address, date of birth, etc.), IC card number, and 100% ID authentication.
At present, the access control system has been widely used in schools, communities, government, company gates, factories, military agencies, office buildings, hotels and other institutional departments. Not only establish a standardized image, but also greatly improve the overall efficiency of the work and management of the security environment. Compared to a traditional lock, a person manages the door. The access control system has absolute advantages in terms of security and cost. The open ID card access control system developed by Shenzhen Yanteng integrates openness and security.
Open: All people can open the door with a valid ID card
Security: ID card as the most powerful proof of each person's identity, directly proves who is the card-wielding person, so as to advance the deterrence of bad attempted personnel to enter the bank, and also provide strong evidence after the accident.
Fourth, system composition and function
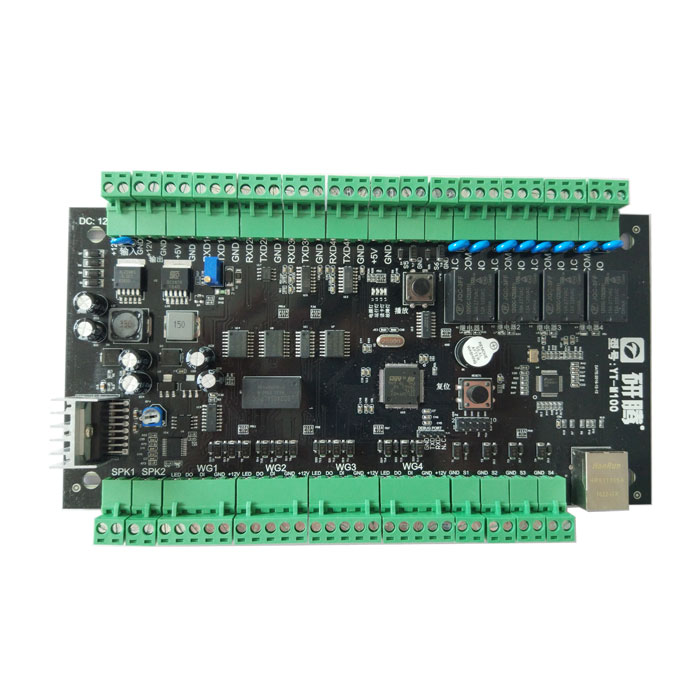
Identity card reader: reading the complete brush ID information, reported to the control panel.

Access Control Panel: Compare the uploaded door opening information and open the door with power off. And save the information
ID card access control software
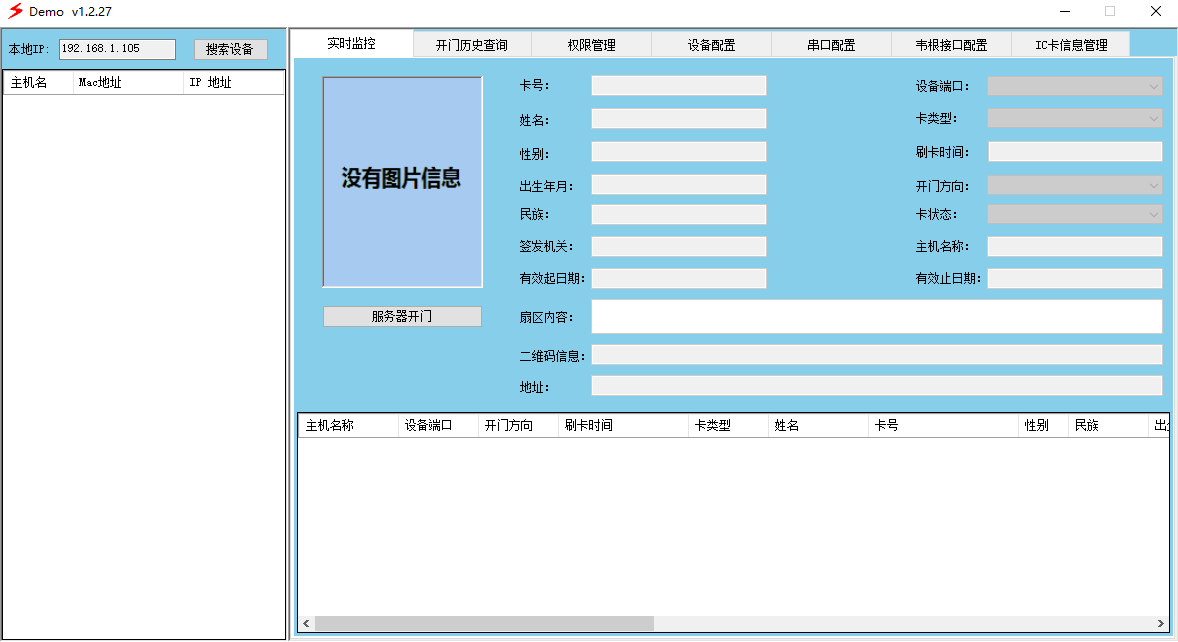
System parameter settings: set the basic parameters of the system, such as personnel grouping, time period setting, permission and time limit settings, etc.;
Access control parameter settings: set the controller's various parameters, such as date, time, etc.; also downloaded to the access controller;
Access control rights management: The unified management of the personnel's authority and time limit can be set and downloaded in two ways: individual and group;
Real-time monitoring: Real-time display of information such as photos, card numbers, and card-swapping time of the card-wiring personnel;
Information query: Real-time query of the credit card record of a certain access point, query all credit card information at any time, and facilitate management;
Report management: The system has a custom report system, users can design their own reports according to the actual situation, or adjust the designed report;
Statistical printing function: You can inquire and print credit card information of a certain date segment, can print the statistical data of printed cards according to statistics of daily, monthly, and custom time periods, and can query and print all the access control credit card information of any date segment;
System operator management: Can establish different levels of system operators, and set passwords and permissions to facilitate system management and maintenance.
March 08, 2024
November 29, 2023
इस आपूर्तिकर्ता को ईमेल
March 08, 2024
November 29, 2023

Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.

Fill in more information so that we can get in touch with you faster
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.